The digitalization of products and services has brought about a significant transformation in terms of the way organizations and individuals work today. Paperwork is minimal, and every task is available on the web. There are several advantages to digital tech taking over our lives, but one significant risk that every organization and person faces today is a cyber attack. There are innumerable ways to penetrate your digital document lockers, from data breaches to cyber attacks to hamper important information.
Figure 1: Different types of penetration testing.
Image credit:
This imminent threat has led to cyber security, in-house or that offered by cyber security service providers, becoming the ultimate defence that every organization looks forward to while setting up their data management systems. After the security systems are in place, the next step is to evaluate how much pressure they can handle. One of the best ways to do so is penetration testing or “pen tests”.
Cyber security service providers in the USA and worldwide rely on pen tests to ensure their digital walls of defence can take on attacks and data breaches that every security system is vulnerable to.
Penetration techniques are used to test the performance of IT infrastructure security for various reasons. Some of them are to ensure user data is secure and identify the vulnerabilities in the security systems.
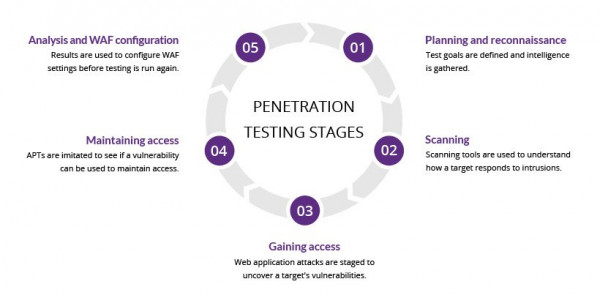
Image credit: imperva.com
Figure 2: Various stages of penetration testing.
This article aims to explain the various types of pen tests used by cyber security service providers to test their IT infrastructure security that can help reinforce the firewalls that keep data safe.
- External testing – External pen tests target those assets of an organization that are visible to the world on the internet. These include their web applications, email and domain name servers (DNS) and the company website. These tests aim at gaining access to and extracting valuable data.
- Internal testing – An internal tester accesses an application behind its firewall and simulates an insider attack. This isn’t necessarily simulating an employee gone rogue but also scenarios such as stolen credentials via a phishing attack.
- Blind testing – A blind test involves a tester with limited information, such as only the name of the organization being attacked, without knowing what is being attacked. This allows a tester to simulate an attack closest to an actual application assault.
- Double-blind testing – Service providers offering cyber security managed services to organizations use this technique to simulate the kind of attacks and attempted breaches they would have no time to prepare for. Double-blind testers don’t have any prior knowledge of the simulated attack.
- Targeted testing – Tester and security personnel sit together and work with each other. They quality check each other’s work and this turns out to be a great training exercise that provides the cyber security team a real-time understanding of a hacker’s perspective.
Conclusion
After the pen tests are carried out, the next step is to perform the risk analysis and prepare a report to work on the identified vulnerabilities. While there are disadvantages of conducting penetration testing, including potentially causing costly losses of sensitive information, encouraging hackers, or exposing your network to cyber criminals, it is necessary to ensure that all cyber security services are up to date with the latest technological advancements.
STL Digital’s team of specialists can help you identify the gaps in your IT infrastructure security and fix the vulnerabilities.
FAQs
1. What are the tools available for penetration testing?
There are several tools for pen tests. While some are used to exploit and collect information, such as Zmap, Xray, SimplyEmail and more, others are used to detect vulnerabilities. Some tools for the second job are MobSF, sqlmap and ZenMap.
2. What other techniques exist to find security vulnerabilities within an organization?
Along with pent tests, auditing the network assets and building threat intelligence frameworks can help identify and resolve security vulnerabilities in the system.
3. How often should organizations do a pen test?
Organizations should conduct a penetration test at least once a year to ensure their IT and network security management is consistent with the new technological trends.
4. What is the difference between penetration testing and vulnerability assessment?
While vulnerability assessment stops detecting them in a network or a system, pen tests exploit those vulnerabilities to penetrate the system.
 areusdev.com
areusdev.com