Vulnerability analysis is essential in protecting digital infrastructure. They provide organizations with the power to identify potential threats and understand their associated risks, to equip them with precise data necessary for a successful defense against malicious attackers. Through automated testing tools such as network security scanners, vulnerability testing teams can help guarantee an organization’s preparedness by delivering comprehensive risk profiles that detail any weaknesses within a system or application – giving businesses peace of mind knowing they have taken all steps possible to protect themselves from cyber-attacks.
Every day, companies and individuals risk becoming targets of cyber attacks. Without proper security measures in place, these threats can cause devastating damage to an enterprise’s IT systems – but with the right vulnerability testing framework put into action, such damages can be greatly minimized. Furthermore, it is essential for those subject to frequent attack attempts; a comprehensive analysis combined with robust management processes provides vital protection against unwanted invasions.
Why is This Important?
Evaluating a system’s vulnerabilities may help a company strengthen its defenses. It also explains how to figure out how dangerous certain vulnerabilities are. In doing so, the company gains insight into its resources, security holes, and overall risk, lessening the possibility that a hacker may penetrate its defenses unnoticed.
Vulnerabilities, such as improper program design, insecure authentication, etc., may be found in the system by scanning the operating system, application software, and network.
Methods for Performing a Vulnerability Analysis
You may do a vulnerability testing by following these steps with the necessary equipment:
1. locating assets
To begin scanning, you must first select what you want to scan, which is not necessarily a cut-and-dry process. However, a lack of insight into the digital infrastructure and the devices linked to it is a prevalent cybersecurity issue for businesses. The rise of mobile technology, the Internet of Things, and cloud computing are all contributing factors.
While it would be ideal for working in a flawlessly organized company, most of us know this is seldom the case. You can feel overwhelmed if you’re trying to keep up with everything that various teams are putting online or updating. It’s hard to protect something you can’t see. Therefore, this lack of transparency is problematic. Fortunately, this process may be automated in many ways, including the discovery stage.
2. Setting Priorities
Once you have an inventory of your resources, the next issue is whether or not you have the funds to do a vulnerability analysis on everything you own. Ideally, you would do vulnerability scans on all of your systems regularly. However, when a company’s budget isn’t large enough to cover every asset it possesses, prioritization might assist in offsetting the suppliers’ per-asset pricing.
3. Identifying Points of Weakness
Scanners for vulnerabilities aim to locate potential security holes and provide advice on how to repair them. There is a wealth of data accessible concerning susceptible software since these vulnerabilities are often publicized in the public domain. Vulnerability scanners use this data to locate weak points in an organization’s network.
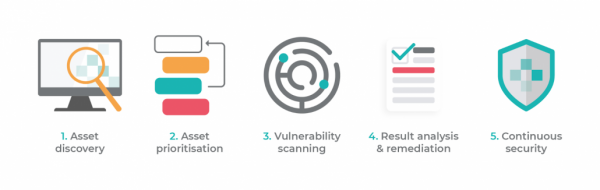
Image Credit:- www.intruder.io Vulnerability Assessment Made Simple a Step-by-Step Guide
4. Assessing Results and Making Adjustments
When the scan is finished, an evaluation report is sent to the user.
A vulnerability scanner should assign a severity rating to each possible flaw it finds. Plan to address the most critical vulnerabilities first, but don’t ignore the others indefinitely.
It is important to keep in mind that not all vulnerabilities exist on systems that are accessible to the general public when thinking about vulnerability exposure. For example, any attacker searching the internet might potentially exploit a system that is accessible through the internet. Thus, fixing any security issues with these systems should be a top priority.
5. Constant cyber defense
A vulnerability analysis is a time snapshot showing all the security holes in an organization’s network. Nonetheless, the company may become exposed again due to fresh installations, configuration changes, newly identified vulnerabilities, and other circumstances. This is why vulnerability management shouldn’t be a one-and-done deal but rather an ongoing activity.
Types of Vulnerability Testing
Vulnerability analysis reveals the many flaws present in a system or network. That’s why it’s crucial to use a wide range of scanners, tools, and approaches throughout the evaluation phase, so that any potential flaws and dangers may be found and eliminated.
A few examples of vulnerability assessment scans are as follows:
- Scans conducted on a network can find vulnerabilities in network security. It is possible to find weak points in both wired and wireless networks using this sort of scan.
- Vulnerabilities on servers, workstations, or other network hosts may be identified via host-based scanning. Scans of this sort often look at ports and services that may be discovered via network scans. However, it provides better insight into the configuration settings and patch history of scanned systems, even older ones.
- Scan results for an organization’s Wi-Fi networks often highlight potential weak spots in the wireless network’s physical architecture. A wireless network scan may verify a business’s network security configuration and discover rogue access points.
- The application scans and checks test websites for common software flaws and misconfigurations in networks and online applications.
- Scanning a database for vulnerabilities may help protect it against assaults like SQL injection attacks.
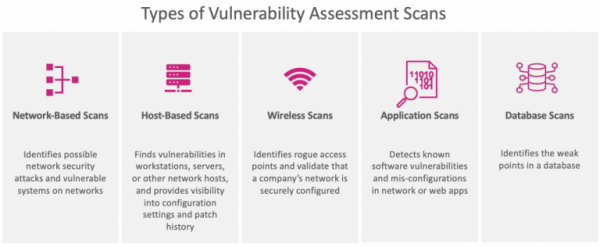
Image Credit:- www.balbix.com Types of Vulnerability Assessment Scans
How Can I Know Whether a Vulnerability Assessment is Necessary for my Business?
Check the efficacy of security measures taken earlier in the SDLC via a vulnerability assessment. For instance, compared to a company that doesn’t educate its developers in safe coding practices or does security architecture and source code reviews, the former is likely to have fewer vulnerabilities.
Vulnerability testing is essential to establish a rock-solid security approach, whether your company develops its own apps or relies on third-party applications. This should be done yearly or when substantial modifications are made to the applications or application environments.
Conclusion
Vulnerability assessments are the front lines in your cyber security defense. Without them, you could easily have vulnerable areas of your network ripe for exploitation by malicious actors. Think about it like a battlefield – if there’s an enemy in sight, they can be taken out with relative ease, but those unseen foes that lurk behind walls and around corners?
That’s where vulnerability scanning comes into play: sweeping up hidden threats before attackers ever had the chance to use them against you! As great as this process is though –the best part might just be how easy it is to do yourself or even automate completely! Get rid of potential enemies now, so you don’t spend much time regretting them later on; invest wisely in efficiently uncovering vulnerabilities today.
