In 2020, each human being created an average of 1.7 megabytes of data per second. With everything moving to the cloud, companies continue to gather data and centralise it at an unimaginable speed. Several people both inside and outside the organisation are being granted access to this data. The expanse of data access has increased the vulnerability of an organisation to cybersecurity threats. With technological advancements, cyber adversaries are no more limited to small-time individual hackers, but include hierarchical organisations operating through the dark web. Therefore, no company in the world is ‘insulated’ against cyber threats. This is where the growing need for and importance of cyber resilience and cyber posture comes into the picture.

The below blog examines the various facets of cyber resilience and cyber posture. It also helps answer a few critical questions.
What is cyber resilience and cyber posture?
Cyber resilience refers to the ability of a business to protect itself against the risk of security incidents by utilising the required tools and processes. A cyber-resilient enterprise is prepared for any unforeseen crisis, challenges, adversities, and threats. The organisation can defend itself against such attacks and ensure its survival regardless of any attack.
The cyber posture of an organisation is the combined security status of all its software, hardware, services, and networks. It is also a measure of how secure the organisation is after the deployment of all its security measures including the security solutions, employee training programs and even the anti-virus. It is the level of cyber readiness of an enterprise.
Are the concepts of cyber resilience and cyber posture interlinked or independent?
Cyber resilience and cyber posture are related to each other; however, they are not the same. There are a few overlapping areas. It is important for businesses to understand the difference between the two to avoid vulnerabilities. In general, cyber posture is a preventive tool while cyber resilience includes both proactive prevention and reactive recovery (of data and files).
Cyber posture refers to the defences incorporated for identification, prevention, and quick response to cyber-attacks before any damage is caused. These include all the measures such as network-level protection, anti-phishing, antivirus, and even employee training meant to prevent business disruption. Although cyber resilience includes preventive protection, it also incorporates purpose-built measures meant for ensuring business continuity.
The efficiency of cyber posture can be measured by the number of breaches prevented and the percentage of cyber attacks evaded. However, the success of cyber resilience encompasses recovery time objective (RTO), recovery point objective (RPO) as well as total system uptime.
What businesses need to know to evaluate partner cyber resilience?
An increase in the number of high-profile security breaches have highlighted the importance of building cyber resilience. Since a business cannot operate without its customers, it is important to evaluate a partner’s cyber resilience. The presence of a transparent and reliable evaluation process limits the overall risk of cyber-attacks.
Below are the parameters to keep in mind for evaluating a partner’s cyber resilience:
- Existing data protection standards: Protecting data and recovering it in case of an unforeseen attack is essential for any organisation. The inability of an enterprise to recover data on account of a partner’s fault may lead to unanticipated setbacks. This makes it necessary to enquire the details of the partner’s existing data protection policies and backup strategy.
- Endpoint security strategy: End-to-end security is critical to protect an enterprise against possible data thefts. With remote working likely to continue, inquiring about the endpoint protection of the partner helps develop the confidence to trust their cyber security posture.
- Consistency in security policies: Make sure that the partner has a standard policy for all the security measures. For example, critical policies such as firewall/VPN usage, access control and restricted usage etc, must be standardised across an enterprise. In addition, a cyber resilient partner would also make efforts to keep employees well-informed of the latest cyber security trends.
- Regular security audits: Security audit helps an enterprise understand the security risks of a systema and reduce the impact of those risks. Have a discussion with your prospective partner about your likelihood of obtaining access to their security logs in case a breach occurs.
What are the pillars (technical) of cyber resilience and cyber posture?
The objective of cyber resilience is to ensure that an organisation maintains its critical business operations.
The 4 pillars of cyber resilience are:
- Anticipate: The framework begins with anticipation of threats. It includes understanding the risk posture and threat modelling. One major benefit of this pillar is that it helps in developing a proactive approach to thwart cyber-attacks.
- Withstand: Withstand pillar limits the impact of a cyber-attack. To accomplish this, IT reroutes users as well as systems and performs activities to maintain business operations. Cyber operation teams take care of incident management. However, an organisation must plan a certain course of action to make all this work.
- Recover: Majority organisations rely on their disaster recovery plan which helps restore critical business data. However, the plan does not account for recovery of services and data-related workstreams. Successful recovery of a system implies restoring platforms, networks, and applications.
- Adapt: A cyber-resilient organisation analyses its readiness against an attack. Therefore, business leaders make changes to the cybersecurity framework, architecture and even business functionalities to better prepare themselves for future attacks.
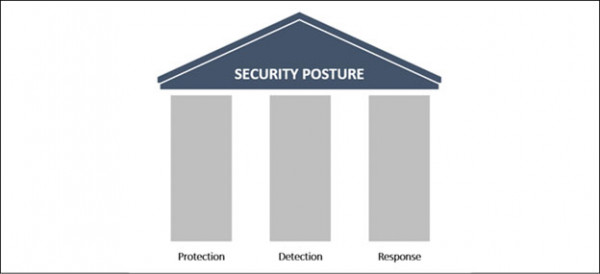
The pillars of cyber posture are:
- Prevention: It emphasizes on employee training, penetration testing, vulnerability assessment and exercises to help an enterprise handle cyber-attacks in real-time.
- Protection: Protection includes all the possible measures an organisation adopts to stop an attack. Most organisations deploy firewalls, antivirus, domain name system filtering, endpoint protection and geo-blocking to secure their enterprise against potential cyber threats.
- Detection & Response: The detection of a threat and responding to it as per situation are given the highest priority by information security personnel. Organisations also acknowledge that it is better to spend resources to detect an attack and respond as required. A few well-known detection & response tools are SIEM (Security Information Event Management), SOAR (Security Orchestration Automated Response), IDS (Intrusion Detection System) and UEBA (User Entity Behavioural Analytics).
Which companies are offering partner programs?
Majority of cyber security service providers offer cloud security, endpoint security, email security, and network security services. McAfee, Cisco, Check Point Software, Symantec, and Palo Alto Networks are the leading enterprise-grade cybersecurity service providers.
How is STL Digital helping companies build cyber resilience?
STL Digital carries forward STL’s legacy of more than 25 years in advanced network technology and integrated digital networks. We help industries and businesses reimagine their digital future. With the convergence of next-gen technologies like internet of things (IoT), 5g and quantum computing, the risk of cyber attacks has increased manifold. STL Digital brings together capabilities in various areas such as software, technology, processes, machine learning and behavioural sciences. We facilitate organisations in developing an ever-evolving cyber posture through optimization of their cyber investments.
How are STL Digital’s offerings are differentiated?
With three decades of experience in digital transformation, STL Digital is all set to accelerate businesses worldwide with its ‘digital-first’ solutions. Leveraging our digital transformation capabilities, we work enthusiastically with a start-up mindset. Our motto is to try early, and if it doesn’t work, fail fast and move on to our next step. We engage ourselves in creating new-age digital services. This helps dynamic organisations embrace innovative business models that open doors to potential revenue streams like never before.
How can the right partner be a game changer for organisations?
In the last decade, enterprises worldwide have utilised technology and digital capabilities for their growth. Due to this, they have also attracted cyberthreats. Managing the increased risk of cyber attack is essential for organisations to leverage the value of digital transformation and technology. Therefore, the adoption of a vigilant, resilient, and secure approach supports an organisation to successfully combat cyber security challenges.
The right cybersecurity partner helps you in understanding the impact cybersecurity vulnerabilities can have on the business. The partner would proactively ensure that deployment of security measures such as EDR (Endpoint Detection and Response), DNS protection, detection, monitoring, and patching does not disrupt regular business operations. At present, an enterprise needs innovative tools and technologies to protect itself against security threats. The right cyber security partner tests the tools for efficiency, communication, and security before implementing them for the enterprise.
How has the changing work environment after the pandemic increased the need for effective cyber posture?
The digital response of organisations worldwide to covid-19 pandemic led to a rapid increase in the demand for digital capabilities. However, the demand also created new cybersecurity risks due to a shift to a remote working environment. Like it or not, work from home environments does not offer the same level of protection as compared to a safeguarded office network set-up. Therefore, the pandemic gave cybercriminals an opportunity to exploit the vulnerabilities of a remote workforce. They also took advantage of people’s interest in news related to covid. Between February and May 2020, OpenBullet, a hacking tool was used to steal personal data from video conferencing services of nearly 0.5 million people worldwide.
With remote working continuing even post-pandemic, companies should proactively plan and prepare for prevention of cyberattacks instead of responding to it. Organisations must change their mindset and accept that breach of data privacy is financially taxing. As enterprises redesign their business architecture post pandemic, they need to acknowledge cybersecurity teams in the form of strategic partners in business decision-making.



